
In Part 1 of this series on securing you Office 365, we discussed using Cloud App Security in Office 365 for detecting account compromises in your environment. In Part 2, we will review what to investigate in Cloud App Security. To use Cloud App Security, you are required to have either the tenant-based subscription or E5 license assigned to your users. For those who don’t have access to Cloud App Security, in Part 3 we will review the Hawk PowerShell Module, which is free – Hurrah! And an alternative which allows you to collect forensic data to review. Let’s get started.
Cloud App Security Investigations
To get started, open the Security and Compliance center.
1. Go to https://protection.office.com and Sign In with your admin account.
2. Click the Alerts drop-down and select Manage Advanced Alerts
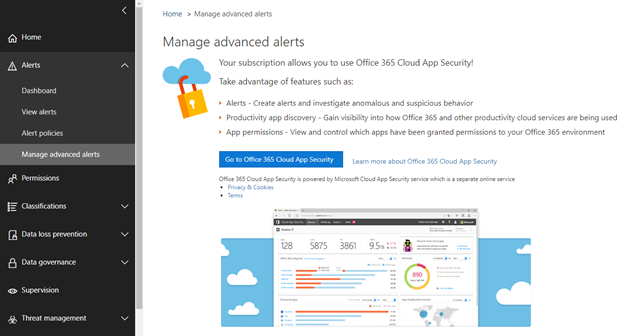
3. Click Go to Office 365 Cloud App Security
4. You are now presented to the Policies Page within Cloud App Security
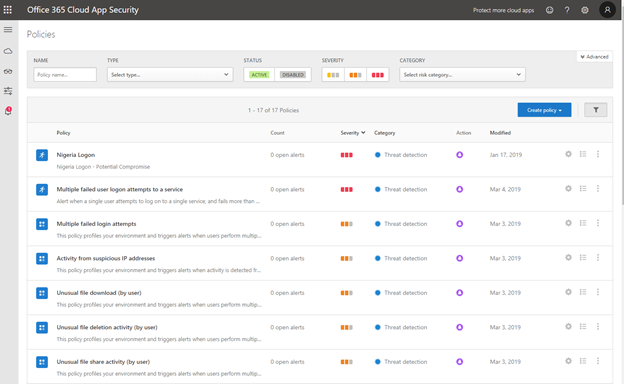
Click on the Alerts Bell and you will be presented with the existing alerts in your tenant. You can filter on the alerts if you would like to review past resolved or dismissed alerts using the search criteria.
Firstly, we’re going to get started by investigating the alerts that have been triggered within Cloud App Security. Below, we can see two alerts, which have been filtered by the Username, here Impossible travel activity and Suspicious inbox manipulation rule are shown as the type of alert.
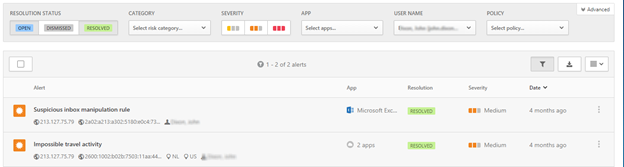
To investigate the Impossible travel activity, we want to select it to collect the following information: username, the IP address and location. These are the three core items needed when you are investigating any alert. Since this alert only shows the impossible travel alert, we will need to review any other alerts triggered.
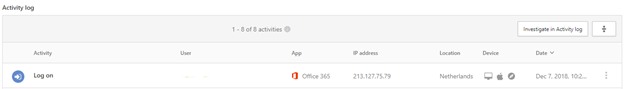
We can see the alert triggered provides an IP address and location of the Netherlands for this attack. In this instance, you will want to mark the IP and location for your incident log. This user also triggered a malicious inbox rule, so our next step is to investigate this further.
The next step is to go back to the alerts page and Click on the Suspicious inbox manipulation rule alert.
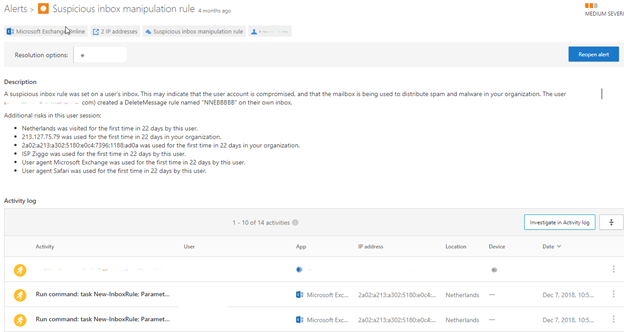
Here, we see a new-inbox rule with the name “NNEBBBBB” which was created to delete messages. If you click on the running man icon to the left of the activity, there will be a drop-down which will supply you with more detailed information on the breach.
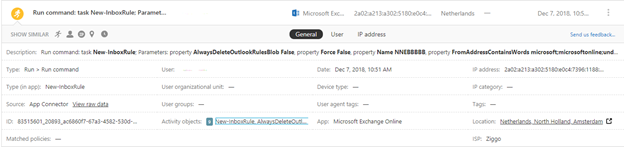
You can now see most of the information in the description. For a more detailed and itemized account of the breach, click on Activity Objects and a new window will pop up with easier to read detailed information.
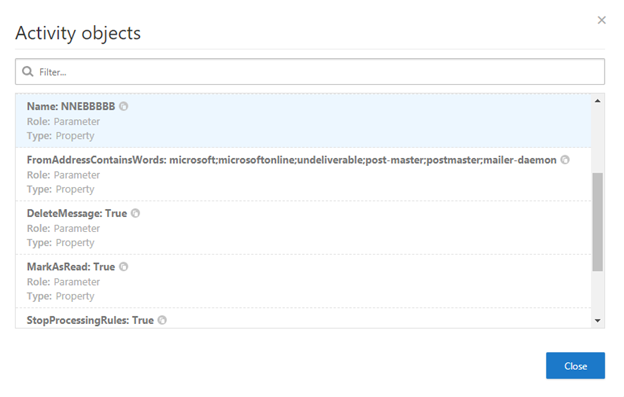
Now we know from our investigation that a new inbox rule was created and the setting FromAddressContainsWords: Microsoft, microsoftonline was set to delete any emails matching these words. You’ve now completed this step, so you can close the Activity Objects window.
In the Alert for Suspicious inbox rule, click on Investigate in Activity Log. This then provides you with all the details of what actions were performed by the attacker.
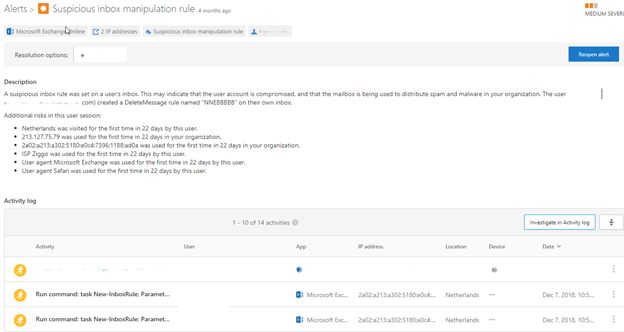
A new page will appear showing activities relating to this activity ID. Once you are in the activity log you can then do a full investigation of what actions were performed. You’ll need a copy of this for your incident report logs in case you are audited or need to review the event again, so export this data to CSV.

Below is what your CSV file will contain:
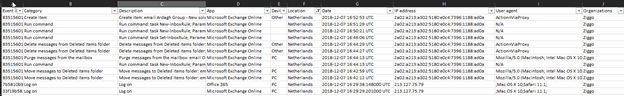
The following columns are included in the CSV download:
- Category: The Activity Performed
- Description: The full details of what actions were performed
- APP: The app used for the connection of the session
- Device: Type of device used, such as PC or phone
- Location: Country attack originated from
- Date & Time of the actions
- IP Address information
- User Agent: details of Mac or Windows and browser types
- Organizations being the ISP provider used during the attack.
Below are the details of this attack, to help you gain an idea of the process the attacker used and how they breached based on the activity log export.
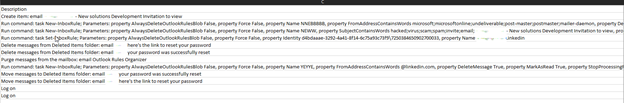
The steps performed by this attacker were the following from bottom to top:
- Attacker logged in with user credentials
- Attacker moved password reset link emails to deleted items folder.
- Created new inbox rule “YEYE” to delete emails “fromaddresscontainswords” linkedin.com
- Deleted password reset emails from deleted items folder
- Created new inbox rule “NEWW” to delete “Subjectcontainswords” hacked, virus, scam, spam
- Created new inbox rule “NNEBBBBB” to delete “fromaddresscontainswords” Microsoft etc.
- Created new email but did not send.
At this point, the attacker was cut off from the system and performed no further actions. We will review how the attacker was cut off in Part 4 of this blog series.
Cloud App Security is a far more efficient and simple way to investigate Office 365 account breaches. The traditional approach using the Office 365 audit log search in the Security & Compliance center for investigating incidents, was time-consuming and lacked the detail you need for logging breaches for audits. During a breach, time is of the essence to understand what the attacker did and what information they might have stolen.
If you don’t have access to Cloud App Security in your organization but want to learn more about how to protect and investigate your environment, stay tuned for Part Three of this series where I will explore the Hawk PowerShell Module.



Thanks for posting Tony.
I was looking at creating a work flow to cover some remediation actions.
E.g CAS Alert trigger for impossible travel > disable user account > password reset
Any idea if such actions are possible using the flow feature?