Customers using Office 365 can use built-in mobile device management capabilities that are included in the service to securely manage their employees mobile devices, including employee-owned mobile devices in a “bring your own device” (BYOD) environment.
The benefits of Office 365 mobile device management (MDM) include:
- Device management – enforce security policies such as PIN/passcode requirements, and prevent jailbroken devices from accessing your corporate data.
- Conditional access – allow access to corporate data only from devices that are managed by your company and that are compliant with your policies.
- Selective wipe – remove corporate data from employee mobile devices while leaving their personal data intact.
Comparisons Between Exchange ActiveSync and Office 365 MDM
Anyone already familiar with managing mobile devices using Exchange ActiveSync may wonder why these Office 365 MDM capabilities are necessary. After all, ActiveSync and mobile device policies are already available in Exchange Online and Exchange Server on-premises. While this is true, the capabilities of ActiveSync vs Office 365 MDM are different, and are designed to solve different problems.
ActiveSync takes a device-centric approach to mobile device management. ActiveSync is used to allow, block or quarantine mobile devices that are accessing Exchange mailbox data such as email, contacts, and calendars. The user-centric controls for ActiveSync extend only as far as enabling or disabling the protocol for a user’s mailbox. Beyond that any allow/block/quarantine is based on device characteristics such as make, model or user agent, even when you are approving or blocking a device for an individual user.
And even though ActiveSync and mobile device policies can be used to enforce security policies such as PIN/passcode requirements, those policies can be circumvented by the connecting device or application as we saw with the initial release of Outlook for iOS and Android.
Furthermore, if a mobile device is not connected to a mailbox using ActiveSync then it is not subject to any policy enforcement at all. With Office 365 this means that the same device could be used to access corporate data using Office Mobile apps and OneDrive for Business without any device security policies being applied. Office 365 MDM closes that security gap by allowing organizations to enforce device management and security policies on any mobile device that is accessing corporate data. Office 365 also takes a user and group-centric approach for targeting policies
The lack of selective wipe in ActiveSync has also been a cause of conflict in the past for many organizations, with employees not taking too kindly to IT administrators remotely wiping their entire mobile device including personal data. The workaround for this has usually been to use a non-native email application such as Touchdown or Outlook for iOS and Android, which sometimes means incurring additional costs to purchase apps, or putting up with limited integration with the device OS and other apps. Again, Office 365 solves these issues by allowing selective wipe.
Device and Application Support for Office 365 MDM
At Ignite 2015 Microsoft presenters used this slide to communicate the device and application support for Office 365 MDM. Basically this means support for iOS and Android versions released in the last couple of years, their native mail applications, and the Office Mobile applications for those platforms. There’s been a few changes since Ignite with the Outlook app on iOS and Android now including compatibility with Office 365 MDM.
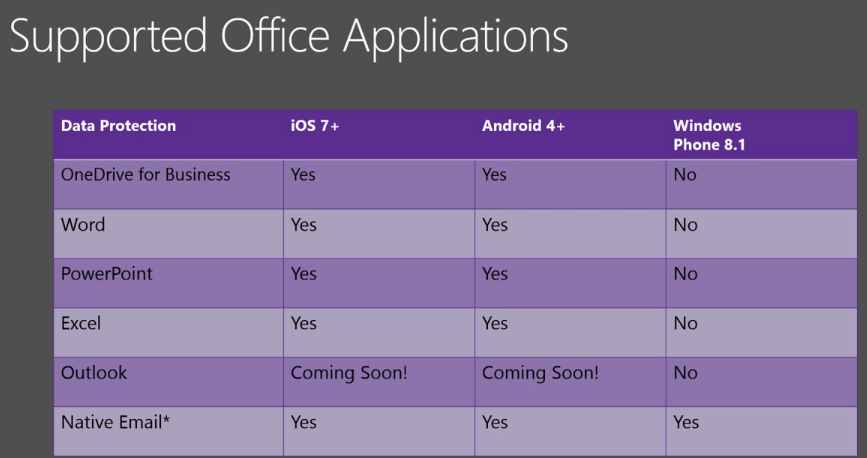
Windows Phone 8.1 is unlikely to be updated to support Office 365 MDM and fans of Windows Phone may need to wait for Windows 10 Mobile instead.
Office 365 MDM Policies for Mobile Devices
The policy controls available for administrators to allow or block mobile devices from connecting to Office 365 resources can be summarised as follows:
- Security settings – device PIN/passcode, including length and complexity, as well as inactivity timeout (device lock) and failed login attempts
- Device encryption – enabled by default in Windows Phone 8.1, enforceable for Android, not enforceable for iOS
- Jail broken device detection – this includes “rooted” Android devices
- Managed email profile – iOS only (email profile is set up automatically, and manually created profiles are blocked)
Depending on the mobile device type a variety of other policy controls are also available, such as blocking screen capture (preventing data leakage by screen capture), blocking app stores, blocking removable storage, and other device feature such as cameras and voice dialling. A full list of policy capabilities for each mobile platform is available on TechNet.
Deploying Office 365 Mobile Device Management
If you are planning to deploy Office 365 MDM for your organization the process involves:
- Audit your existing mobile devices
- Activate MDM for Office 365
- Create MDM policies
- Enrol end user mobile devices
- Ongoing management and reporting



Hi Paul,
I have a query we have Hybrid setup and activesync is working fine on mobile devices as well.
we have default policy Mobile device Mailbox policy for all users.
Since we have enabled conditional access we have seen a trend where users mobile devices are getting quarantined or block and we are receiving below message.
ERROR FROM APPLICATION (IF ANY):
Device cannot be synchronised with the server via Exchange ActiveSync due to access policy that is defined on the server.
When checking the mailbox setting for mobile devices we can see we can allow the devices which are blocked or quarantined.
Since enabling CA what has changed because of which our end users are getting this message more frequently
Also i verified the ActiveSyncOrganizationPolicy and the DefaultAccessLevel is set to Blocked.
Could you please advice
Hey Paul,
I have a scenario to deploy Office 365 default MDM to work with on premises exchange 2016 and is it doable without buy Intune subscription? Does the Office 365 MDM has the capability to support on premises exchange 2016 users?
No, I don’t think O365 MDM can do that. Intune has a connector to make that possible.