Disclosure – The author has been compensated to provide an honest opinion of the product in this review. You can read our full disclosure statement here.
One of the key drivers of efficiency in an IT operations team is automation. Automation can be applied to most areas of day to day administration performed by an IT team, no matter the size of the organization.
In particular, when it comes to help desk and systems administration, automation has many significant benefits.
- Automation improves the accuracy of routine, daily tasks, because it doesn’t rely on humans following step by step procedures.
- Automation improves the efficiency of administrative operations, not only by the faster speed at which an automated process can complete a task, but by scaling easier than human-drive processes without increasing costs.
- Automation better involves managers and auditors in the day to day management of IT.
- Automation enables delegation and self-service for your end user population.
Recently I watched a demo of the Adaxes Active Directory management product by Softerra. As I watched the demo, I couldn’t help but think back to some of the IT departments that I’ve worked in, and their heavy reliance on using native administration tools along with documented, manual processes.
Naturally, there were many areas where those processes would break, either due to inexperienced operators, or due to a high volume of requests causing the team being unable to meet the expectations of their customers. User account creation and modification requests couldn’t be completed fast enough, or had unacceptably long lead times that would frustrate customers. And of course, nothing could be delegated out to business users to handle themselves due to the steep learning curve of the multiple, native management tools required for basic user account management scenarios.
PowerShell scripts are fine, but you can’t hand a PowerShell script to a department supervisor to create their own accounts. Sure, you could create a nice front end for them to use, but the development cost of creating and maintaining custom tools like that is beyond what most IT departments I’ve worked with are willing to invest.
This is where Adaxes comes in. Instead of developing your own tools and interfaces from scratch, Adaxes provides them for you. All you need to do is install it, configure it for your management tasks, and let your help desk and business users do their job using the simple web interface. In addition, you can set up powerful workflows that will run automatically behind the scenes to perform the bulk of the work for day to day administration tasks.
I don’t want to make it sound overly simple. After all, you can’t automate what you don’t understand. Adaxes requires you to understand what your administrative tasks are, how the tasks should be performed in your environment, and have designed your environment (e.g. clear security groups per department) to let Adaxes do the job it’s designed to do.
Not everything can be 100% automated. There’ll be edge cases where direct admin is required, but you can still empower a subset of your IT team to handle those cases, and let the majority of the repetitive tasks be run by Adaxes. There’ll be some upfront investment of time to get things working, but after that the payoff will be significant. That said, it’s preferable that an automation system can give you some quick wins so that you start to benefit almost immediately.
Installing Adaxes – Pleasingly Fast
The installation process for Adaxes was quite simple, and only took a few minutes. I installed a single server, but you can also deploy Adaxes with multiple servers for high availability, and also to service different geographic regions.
Adaxes uses a service account to perform changes in your environment, so naturally that account needs some permissions. I granted mine Domain Admins and Exchange Organization Management, which is the general recommendation from Adaxes. You can cut that back to a lower level of access if you like, once you understand the tasks Adaxes is performing for you and the minimum privileges needed for those tasks.
After granting my Administrator account access to Adaxes I had a quick snoop around the settings, and checked the web administration console. It has a nice, clean look to it, and is fast to navigate.
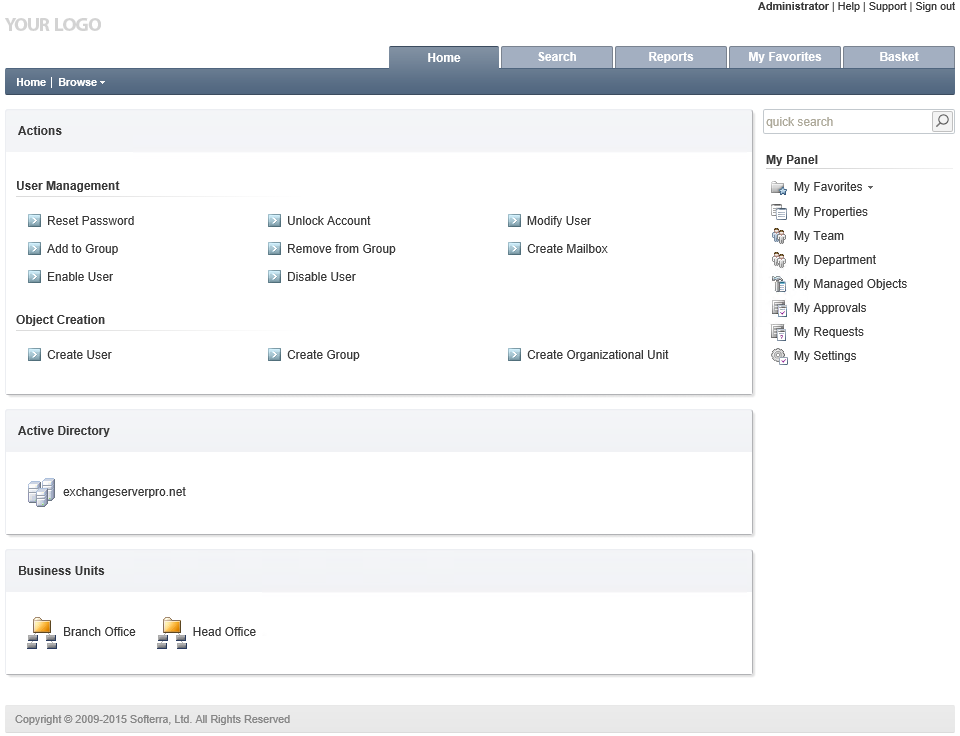
In the Adaxes administration console, which you can think of as the back end to Adaxes, there’s some useful pre-canned security roles, business rules, custom tasks, and scheduled tasks. You can quickly get a sense of what Adaxes is capable of, and see examples that you can either enable as-is, or customize for your own requirements.
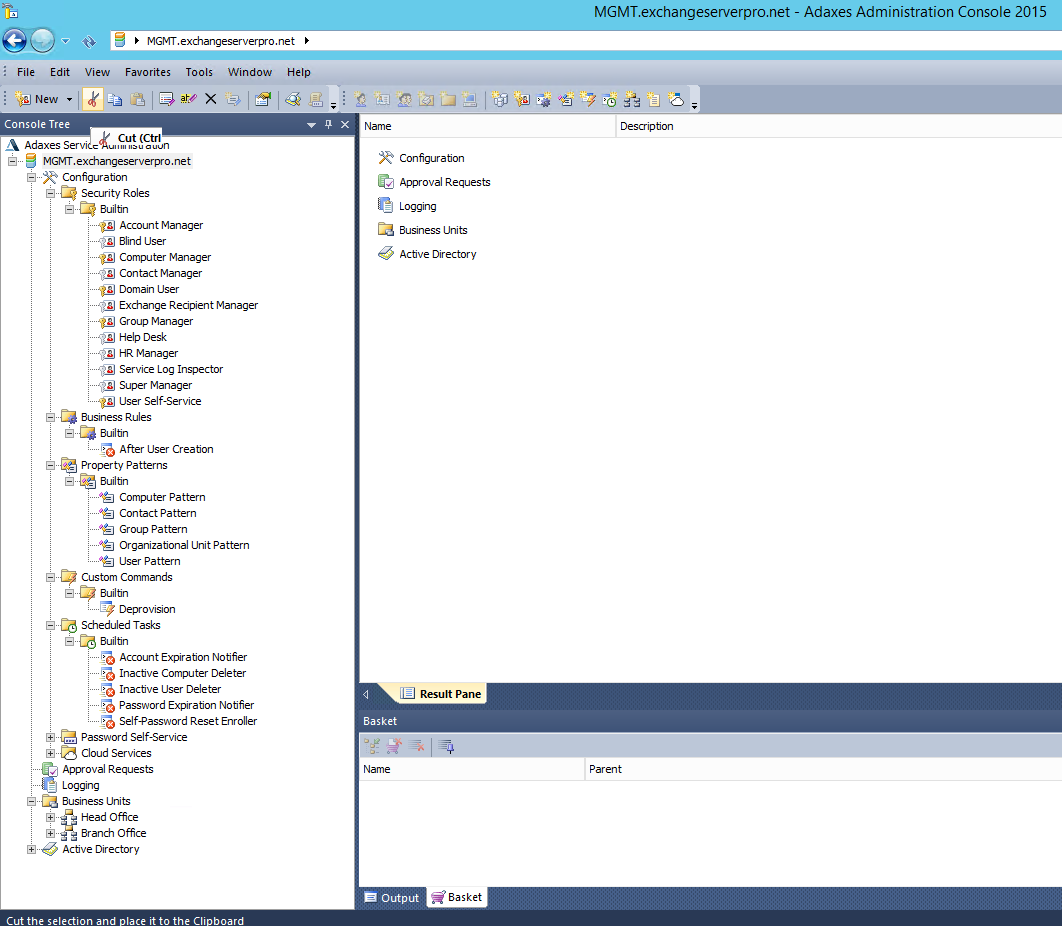
Quick Wins – New User Creation
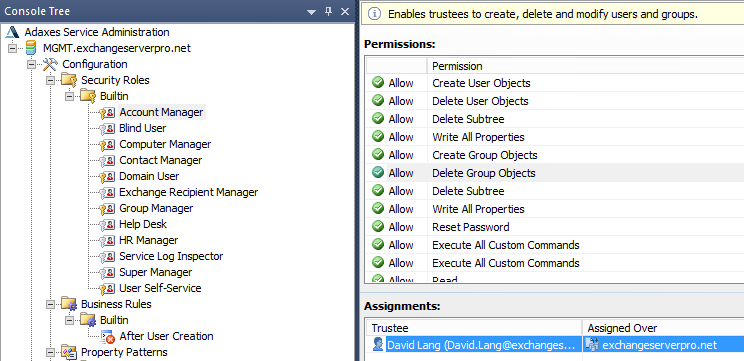
To see just how quickly I could make something useful in Adaxes, I decided to tackle a simple user creation scenario. First, I granted a help desk user, David Lang, the Account Manager role within Adaxes.
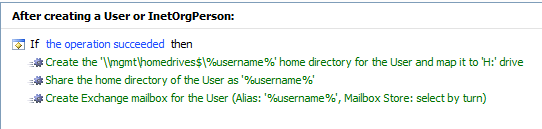
Then, I enabled the “After User Creation” business rule, and made a few changes to the settings to put in things like a real server name for the home drive, and remove some tasks I didn’t need such as Lync provisioning.
One of the capabilities I was pleased to see is the ability to define which Exchange databases a new mailbox will be created on. Yes, we can control this in Exchange itself, but the help desk would still need to know how to use the Exchange management tools to create the mailbox, and there’s nothing to stop them manually picking a database anyway (unless you get deep into customizing RBAC roles).
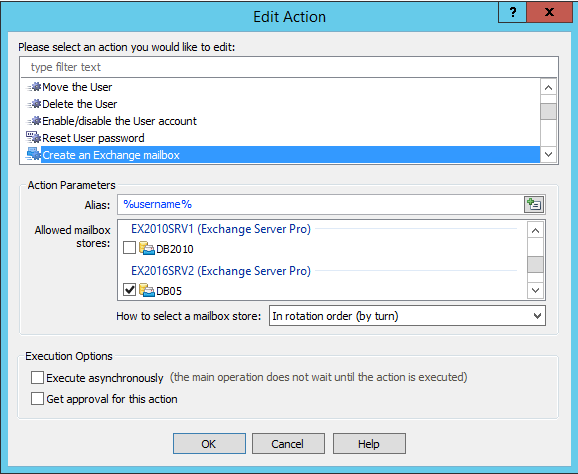
After making those few changes I logged in to the web administration console as David Lang. As an Account Manager, David sees only those tasks that he can perform within Adaxes. Remember that at this stage David hasn’t needed to be granted membership of any privileged Active Directory or Exchange groups, such as Account Operators or Recipient Management.
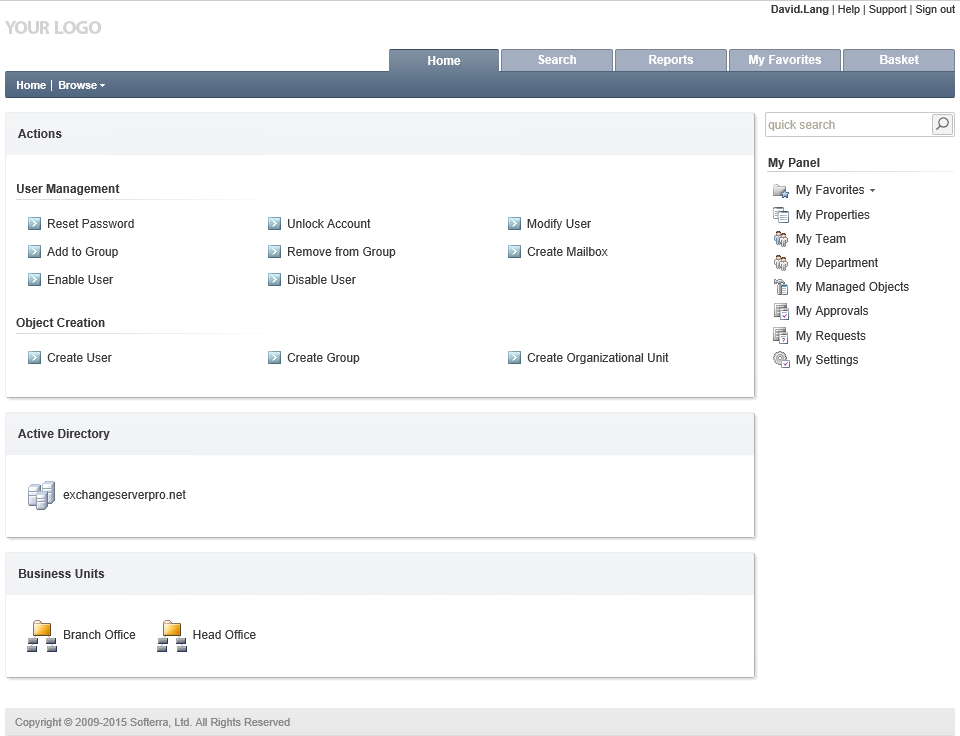
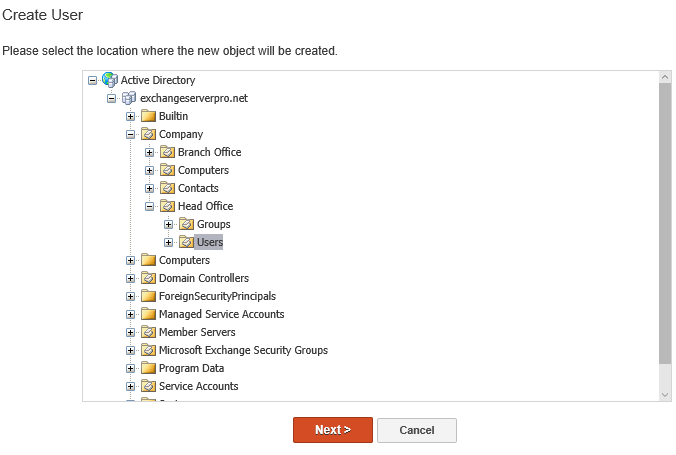
Using the web administration console David can create a new user in the Head Office OU.
David only needs to fill out a few details, generate a password, and click Create.
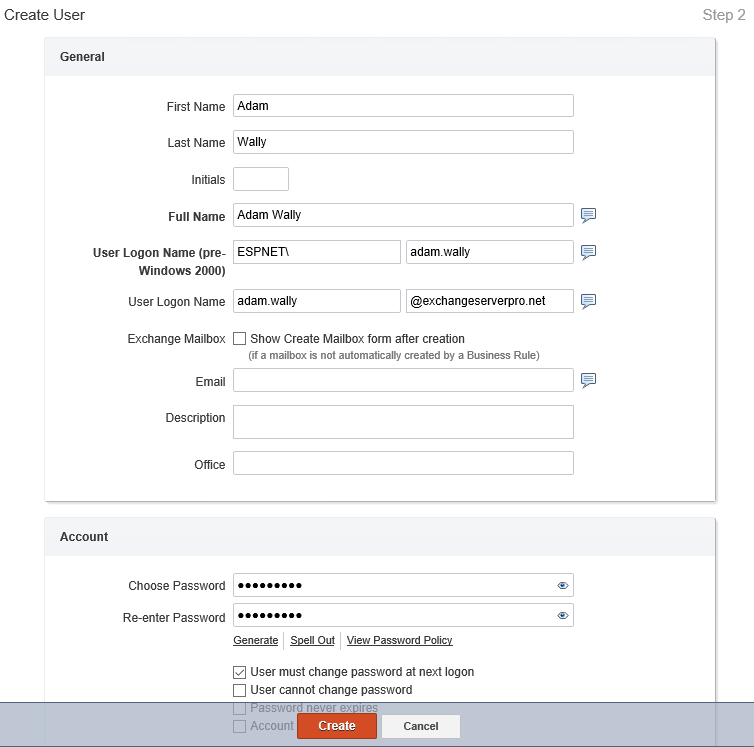
The business rule fires in the background and handles the additional steps for provisioning the new user account.

Within seconds the mailbox is visible in the Exchange management shell.

So there’s a quick win for Adaxes. But I’m not entirely happy with that process straight out of the box. David had too many fields displayed to him that he didn’t need to fill out. And I also want some extra steps performed for new mailboxes in this organization.
Advanced User Provisioning
So let’s take things a step further. I’ve already shown you that user creation is easily automated using pre-canned business rules in Adaxes. But in addition to that basic user creation process, I would also like:
- Users to be created based on different template accounts in Active Directory.
- Only the minimum fields be displayed to Account Managers when they are creating new user accounts.
- New mailboxes to have mailbox audit logging enabled for them by default.
The first one turned out to be simple. To begin with, I created a template account in Active Directory for staff in the Payroll team.

Next, I customized the web interface to add a “Copy User” action to the home page.
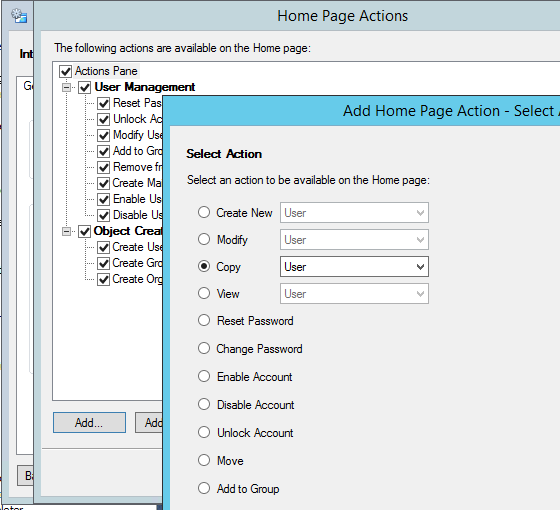
I further customized the action so that it will only display users named “_Template*”, won’t ask any questions about creating a mailbox (since that will happen automatically), and will automatically place the new users in a specific OU. The result is that David now sees a “Copy User” action in his web administration console.
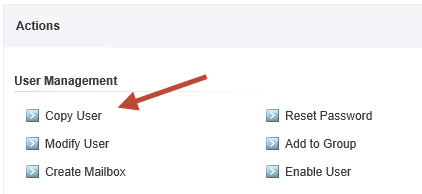
The “Copy User” task that I created only presents the matching template accounts to be copied. I only have one template account in my Active Directory, but it would be simple to scale this task up by adding multiple template accounts for different departments.
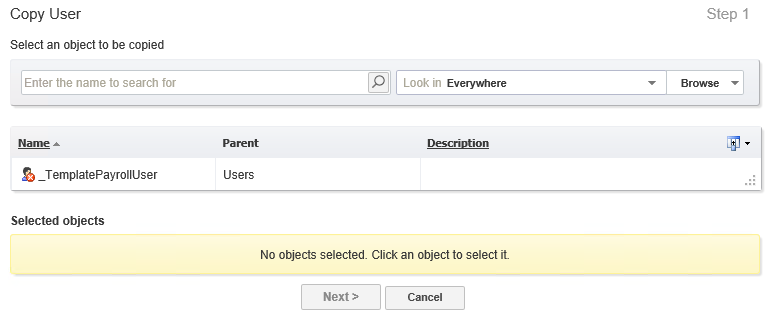
David now sees fewer fields that need filling out during the user creation process, making the user creation process even simpler.
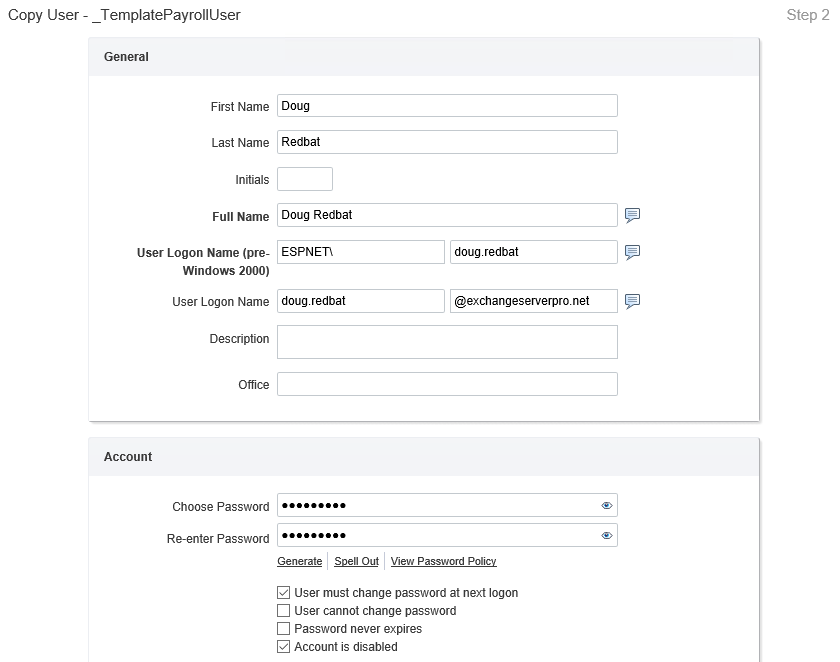
That just leaves mailbox audit logging on my wish list of improvements to the user creation process. After a little digging around in Adaxes I could not find a specific option to make this change. However, I did find that we can run custom scripts as actions in business rules. So to enable mailbox audit logging, I simply needed to add a short piece of PowerShell code as an action.
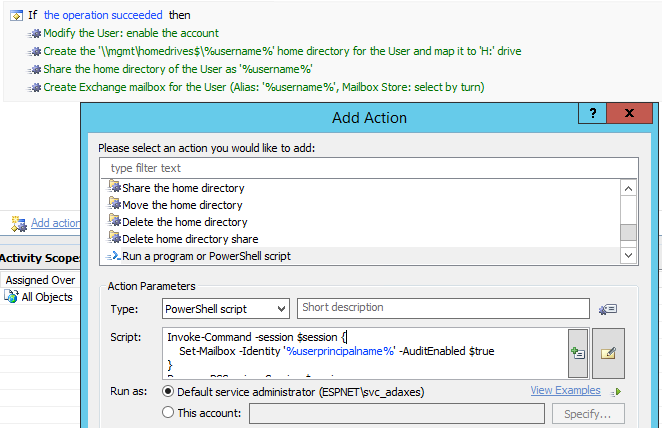
With that simple change, mailbox audit logging is enabled at the time of mailbox creation, which removes the risk of it being missed during a manual process. In the real world I would probably also create a scheduled task in Adaxes that ran nightly to re-enable audit logging on any mailboxes where it may have been disabled.
Self-Service
I’ve shown you how flexible and powerful the user creation process is with Adaxes (although I’ve barely scratched the surface with those examples), but what about self-service? A lot of IT administration involves actioning requests from end users that, quite frankly, they should be able to do themselves.
Password resets are a significant issue for many help desks. Authenticating a person over the phone is difficult if you don’t have the right processes in place. But even if you do, it’s time consuming and unnecessary to be handling every password reset through your help desk.
Adaxes has self-service password reset capabilities included, but not enabled by default. To get this working I only needed to create a new policy for password self-service, and apply it to users. I chose to apply it to the entire domain, but you can be more granular and have different policies for different departments, or different classes of user. Perhaps your highest risk users should require SMS verification, or a higher number of correct answers.

Before a user can use the password self-service features, they need to be enrolled, which only takes a few minutes.

Password reset is a user friendly process. After visiting the self-service page and selecting the “Forgot password?” link, which they could reach from their mobile device or a kiosk machine in your network, the user simply answers their secret questions and then chooses a new password. Your Active Directory password policies are enforced as well.
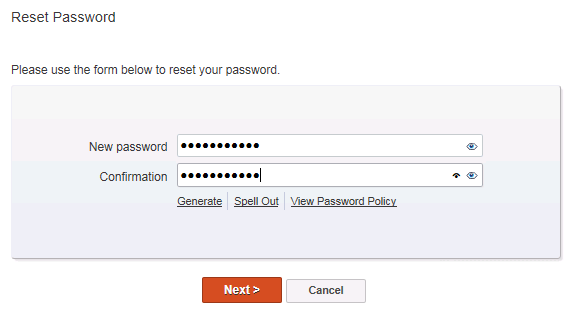
You could also publish the “Forgot Password?” link to your intranet or corporate website. Another option for password self-service is to deploy the Adaxes client to your desktops, so that users can reset their password from the Windows login screen.
Auditing and Reporting
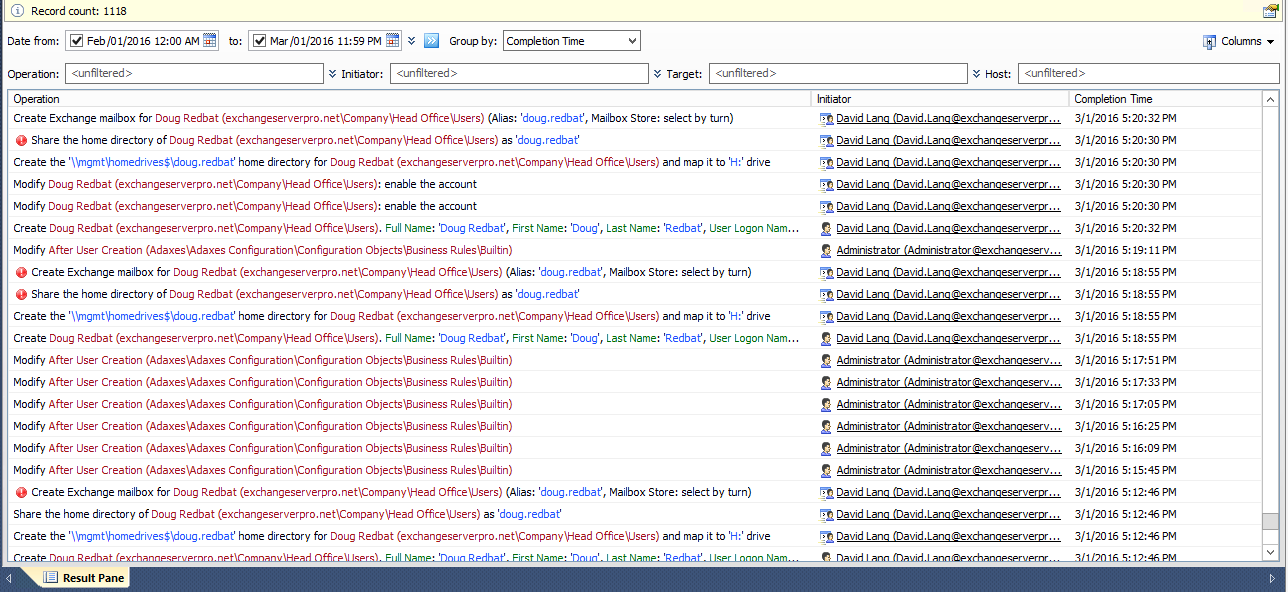
As you can see so far, Adaxes very quickly becomes the centre of your Active Directory management activity. All of the actions that Adaxes is taking occur under the Adaxes service account. So if you were to look at your domain controller security logs, or your Exchange administrator audit logs, you would only see the Adaxes service account making changes and not the initiator of the request.
Fortunately, Adaxes has its own built-in auditing and reporting to track all of this activity that is going on.
What’s the Support Like?
I found Adaxes to be intuitive and user friendly, but as my first time using the product I naturally ran into situations where I didn’t know what I should do next. For most of those situations, I was able to very quickly find an answer in the Adaxes support and FAQ pages. The tutorials are detailed and easy to follow, which is a refreshing change from some of the poor documentation that a few vendors put out these days.
For one scenario, creating Shared mailboxes in Exchange, I wasn’t able to find an answer quickly. Rather than keep hunting, I decided to take the opportunity to test the Adaxes support team, and I logged a ticket through the web site. Two days later, I received an impressively long answer in my inbox with the complete steps required.
Not only that, Adaxes support pointed me to their script repository which already has the PowerShell code needed to set up the tasks for creating Shared mailboxes.
Complete Control?
To be honest, in the few hours that I spent testing this software I struggled to find typical, time-consuming scenarios from my past experience that Adaxes couldn’t handle.
Need to enforce certain naming standards for users or groups? You can do that in Adaxes with property patterns.
Need to place new users in a temporary OU to start with, then move them based on the department or city attribute for their user account? You can do that in Adaxes with business rules.
Need to give your help desk the ability to set an out-of-office reply for staff who are unexpectedly absent, without resetting passwords or granting permissions to their mailbox? You can do that in Adaxes with custom commands.
Need to automate the de-provisioning and removal of departed users from your network? You can do that in Adaxes with custom commands and scheduled tasks.
Need to add approvals so that user creation can be delegated out to the business without allowing them to create unauthorized accounts? You can do that in Adaxes with approvals on business rule actions.
Need to do something that Adaxes doesn’t have an option for? Write some PowerShell (or start with code from the Adaxes script repository), and have Adaxes run it for you.
Final Thoughts
Although I am a big fan of automation, when I first learned about Adaxes I thought that another admin console would not automatically make an IT department more efficient. However, once I saw Adaxes in action I realised it would very easily replace many of the native management tools that IT admins use, such as AD Users & Computers, the Exchange Admin Center, and the collection of custom scripts that tend to build up over time. Since IT admins need to learn all those tools anyway, giving them something as intuitive as the Adaxes web administration console to learn instead can reduce the training burden for new IT staff.
Does it do everything an IT department needs? Of course not. The “single pane of glass” for all possible IT operations in a company is a myth. So why not use best of breed tools where they are needed, instead of a never ending search for one giant tool that does a mediocre job of everything?
Yes, there is an investment of your time required to see returns from Adaxes. But you can implement some of the quick wins almost immediately, such as basic user creation and password self-service, and then work on automating more and more of your routine operations into Adaxes.
What about skills development? Does Adaxes squash the career prospects of low level IT admins by replacing native tools? Perhaps. But there’s nothing stopping those people from learning away from your production environment, then applying their new skills to the edge cases that will surely pop up from time to time, or by getting involved with the ongoing development of automated tasks within Adaxes.
Ultimately, if you’ve got a gigantic administrative mess on your hands today, then Adaxes won’t magically clean it up for you. But without Adaxes driving you to achieve more efficient operations through automation, you’ve still got that gigantic mess on your hands anyway.
Personally, if I was implementing automation for Active Directory and Exchange administration by an IT operations team today, I would seriously consider building it on Adaxes.
Adaxes provides a full functioning 30-day trial. Just download it and give it a try.



AD Manager from ManageEngine is just as awsome. I will definitely have a loom at adaxes too. 🙂
Paul,
I assume Adaxes doesn´t care if the Exchange is off- or on-premise?
Regards
Johannes
Johannes,
It does see the difference between them but in terms of management and/or automation procedures, Adaxes doesn’t care whether mailboxes are on-prem or in the cloud.