Application Inundation
Microsoft Teams applications enhance the user experience by providing seamless access to Office 365 third-party apps and any custom apps you may have developed yourself. These apps play a key role because they enable users to continue working uninterrupted without leaving Teams.
But with hundreds of apps available in the Teams app store, it’s difficult for decision-makers and administrators to determine what apps are beneficial to their organization and necessitate inclusion.
Fortunately, the Microsoft Teams admin center provides the data around each app you need to decide. This article helps you navigate the Teams admin center; explores the various app types available; and provides detail around permission policies, setup policies, and things like Resource-specific consent you’ll want to familiarize yourself with so you can effectively manage Teams apps for your organization.
Types of Apps
Three types of apps integrate with Teams:
- First-Party: These are created and published by Microsoft, and include familiar apps like Forms, OneNote, Stream, and others like Bing News, Power Automate, Dynamics 365, etc.
- ISV: Many ISVs publish apps for Teams, and you’ll find a vast majority of them in the Teams app store.
- Custom: Custom apps are particular to your organization; built and used specifically for users’ business requirements.
The Microsoft Teams admin center allows admins to review the applications available to the organization. Using the Manage apps page, you can interact with apps, which allows you to block or enable apps and publish sets of apps to users through setup policies.
Administrators can also customize or rebrand the app properties for some apps based on business requirements, such as changing the icon color or name to align with the organization’s branding. Additionally, custom app policies and settings enable admins to tailor the app experience for specific users in the organization by implementing app permission policies and app setup policies.
App Review and Licensing
Typically, when I speak to organizations about third-party apps in Teams, there’s always a concern around client data, privacy, and what kind of permissions the app has. Thankfully, you can find all this information directly in the Teams Admin Center to help you understand and review the apps you are considering.
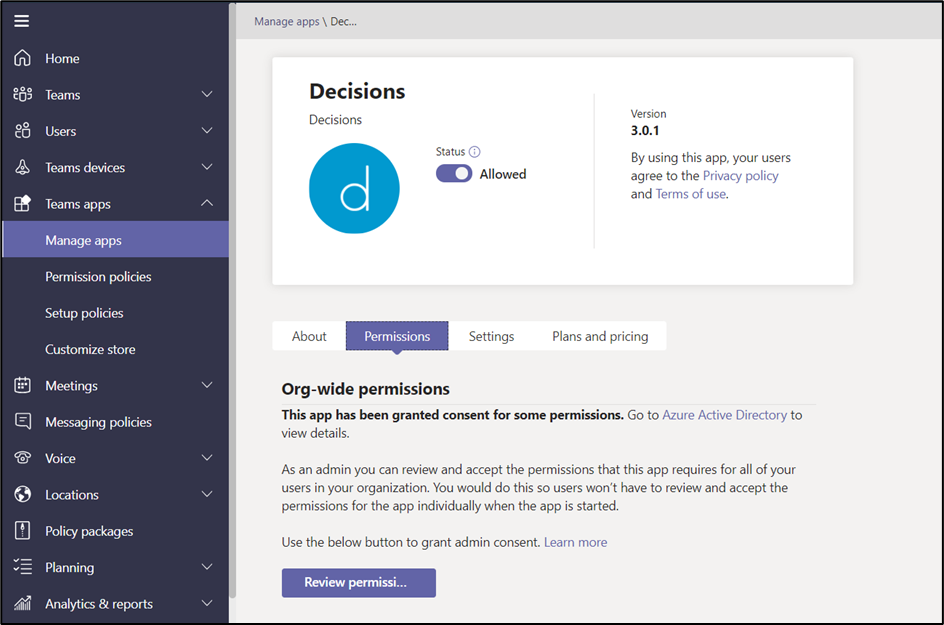
You can select an app in the Manage apps section and view the description, terms of use, permissions, certifications, and even plans and pricing (Figure 1):
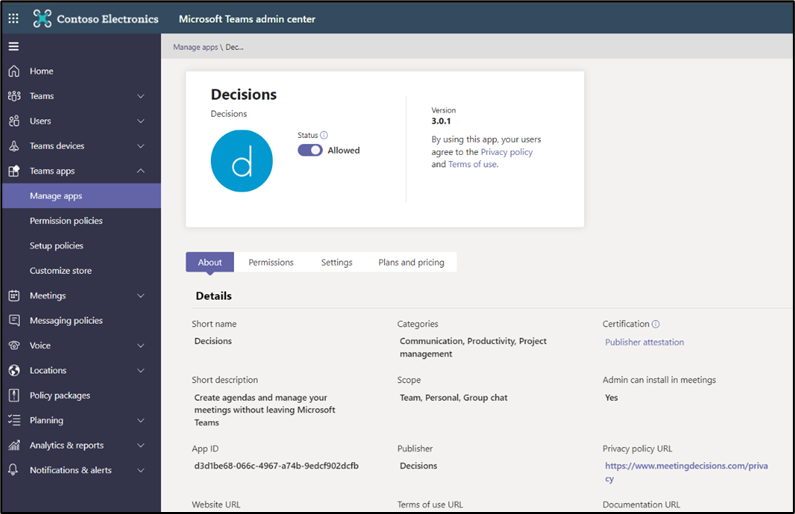
You can install some Teams apps for free, but subscriptions are usually required to experience the app’s full functionality. A paid subscription is often required following some third-party apps free trial periods. These subscriptions are available through AppSource, and some are available through the Microsoft Teams admin center.
Teams Apps Permission Policies
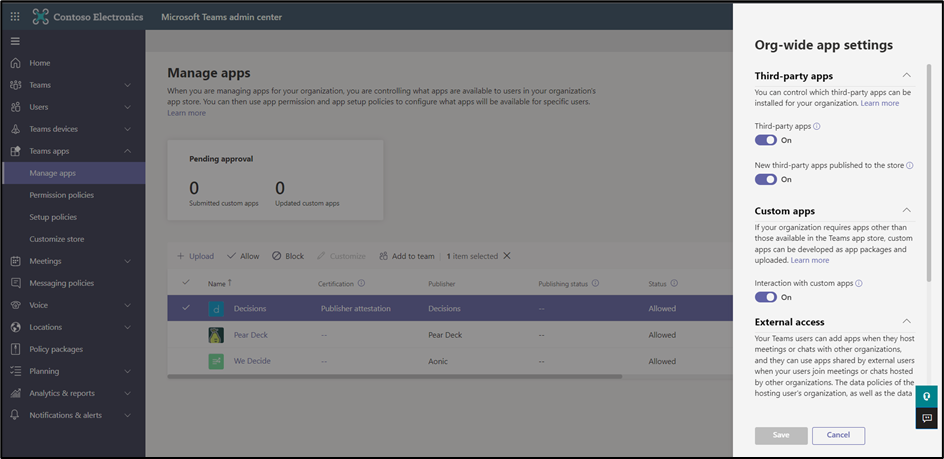
After choosing the apps you want to use, you can control how you present these apps to users. First, make sure your org-wide settings are set to allow third-party apps (Figure 2), so you can control the installation of these apps. If you use Custom Apps, make sure to turn on this setting:
In Permission policies, you can create a policy for either the entire organization or a group of users that only allows specific applications and blocks all others. In Figure 3, the admin has decided to allow two third-party apps for the organization:
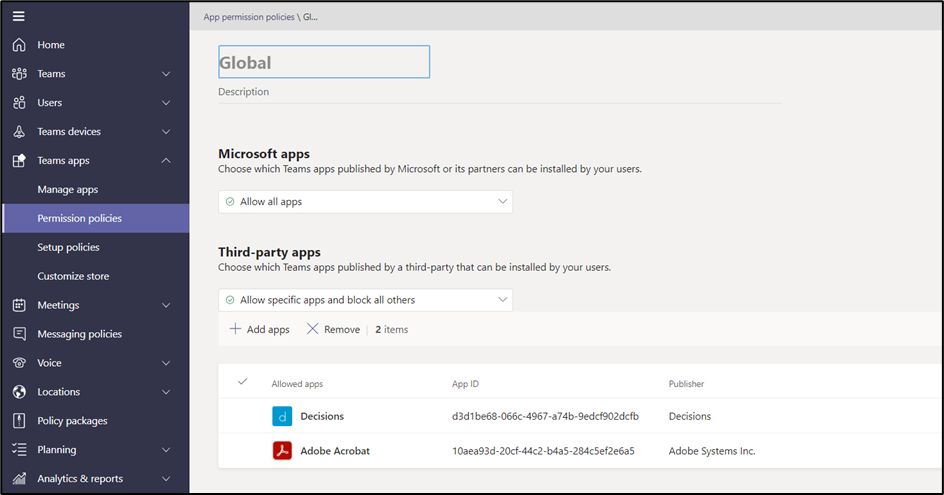
These policies enable you to control which applications can be used in your organization while allowing users to install the apps they need to carry out job functions.
App Setup Policies
Admins can use app setup policies to install and pin apps to the app bar to encourage the use of selected apps and allow or block users from uploading custom apps to Teams. An App Setup Policy can be applied to all users in the organization or a group of users.
In Figure 4, the administrator is updating the Global App Setup Policy. The Global App Setup Policy applies to all users unless a user’s account is assigned to a different app setup policy:
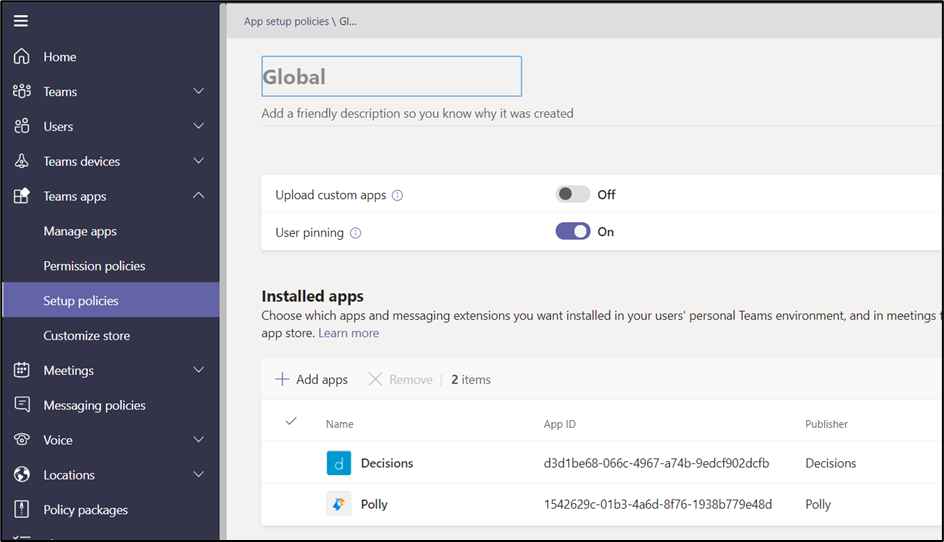
The Custom App setting determines if a user can upload a custom app to Teams via Teams desktop and browser. They can be used on both android and IOS mobile devices, but the user will need to be logged into their desktop to add the apps to Teams. Turning the setting on allows the deployment of custom apps using tools like Power Virtual Agents or PowerApps without submitting the app to the Teams App store.
Installed Apps are apps installed by default so they are readily available in the Teams client. In Figure 4, the administrator adds Polly and Decisions as installed apps, so a user can then add them to Teams.
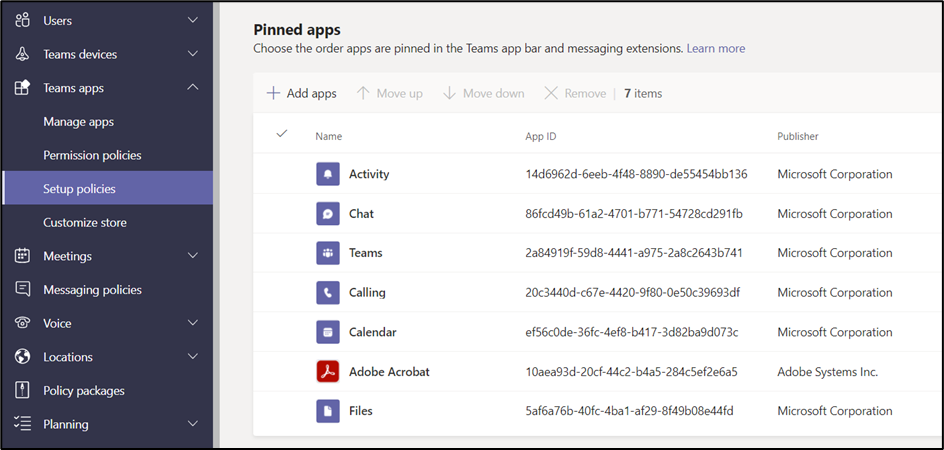
Pinned Apps enable you to customize the Teams App Bar for your users. You can change the order of the apps and even add your custom app or third-party apps (Figure 5):
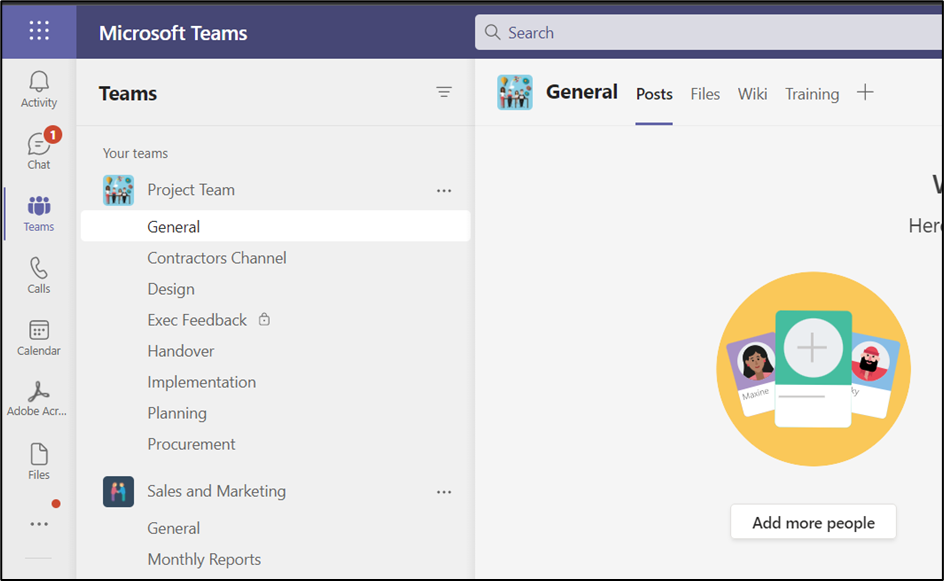
Pinning an app helps promote the app within your organization as the app becomes visible in the app bar (Figure 6). It can take a few hours before the app appears due to the need for clients to refresh their cache:
Read More: Teams + Power Automate: Practical Examples to Automate Tasks
Consent and Teams Templates
Global admins can review and grant permission to apps on behalf of all users within the Teams Admin Center (Figure 7). This lets users start the app without reviewing and accepting the permissions. Some users may not be allowed to accept permissions to apps if you have configured consent settings in Azure Active Directory:
Apps may request permission to read information stored in a team, read a user’s profile, or depending on the app, even send an email on behalf of users. Review the permissions to see precisely what data you allow the app to access and accept if you’re satisfied with the level of requested access. Some applications may ask for permissions that they don’t use, so it’s also worth looking at the Microsoft App Governance add-in, which provides in-depth details of the app including complete app metadata information.
Resource-specific consent
If you’re looking for a more granular way to specify application permissions for Microsoft Teams, then consider Resource-specific consent. Resource-specific consent (RSC) allows team owners to grant consent to an application accessing/modifying data about that team. In effect, RSC enables owners to consent instead of admins only, because the permission scope is reduced to only that team.
This is useful because admins typically don’t have enough information to determine if a specific application should have access to data in a particular team. It also saves administrators time, since as they don’t need to review every application the organization requests. However, you should be aware that not all apps support RSC, so before considering RSC to permission your apps, make sure they are designed to take advantage of the model.
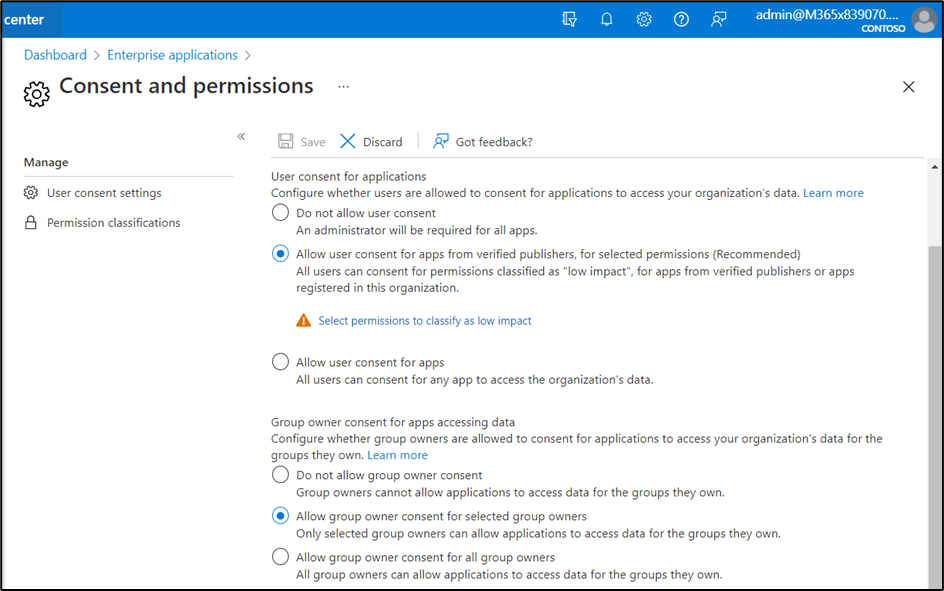
RSC permissions are configured under Enterprise Applications in the Azure AD admin center. The Enable Group-Specific Consent setting needs to be turned on to enable users to consent to apps for Teams that they own. You can find this under Enterprise Applications > Consent and permissions > User consent settings (Figure 8):
Although the granular permissions in RSC are not Azure AD permissions, they are more specific to Teams. Still, learning about the Azure AD application consent user experience is helpful. You can manage applications for your organization and develop applications in a more unified consent experience.
Read more: Use Azure AD Admin Consent Requests to help avoid attacks against your users
Summary
Between varying requirements amongst projects and departments in your organization, over time, you will inevitably end up using a combination of applications within Microsoft Teams. While Microsoft does provide administrators with the tools to support them along their Teams apps journey, it’s important to have a good grasp on policies, pricing, and consent parameters so users can access the apps necessary to collaborate and produce quality work.



thank you – very helpfull